In the rapidly growing crypto industry, the widespread adoption of cryptocurrencies has attracted not only legitimate users but also cybercriminals seeking to exploit vulnerabilities.
Recent findings from cybersecurity firm Kaspersky shed light on a sophisticated malware attack targeting Macbook users in the crypto space.
Harvesting Sensitive Data From Infected Mac Systems
Kaspersky Lab experts discovered that the attackers repacked pre-cracked applications as Package (PKG) files – a type of file format commonly used on Macbooks – and embedded a Trojan proxy and a post-installation script.
The malware-laden applications were mainly distributed through pirated software channels. Once users attempted to install the cracked applications, they unknowingly triggered the infection process.
To deceive users, the infected installation package displayed a window with installation instructions, instructing them to copy the application to the /Applications/ directory and launch an application called “Activator.”
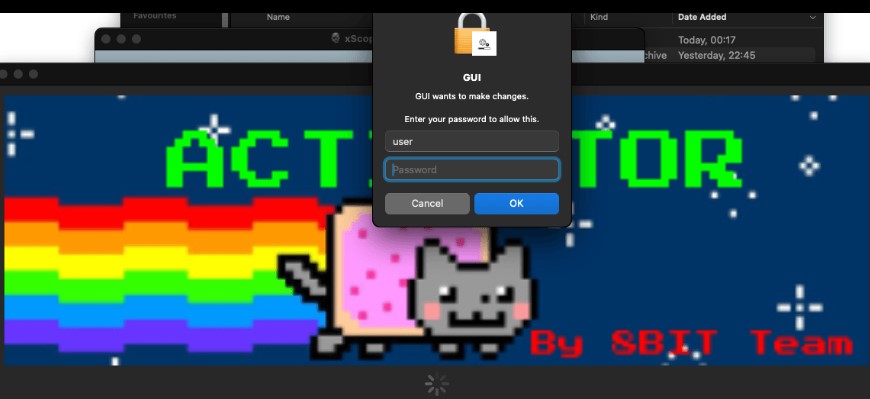
Although appearing unsophisticated at first glance, Activator prompted users to enter a password, effectively granting the malware administrator privileges.
Upon execution, the malware checked the system for an installed copy of the programming language Python 3 and, if absent, installed a previously copied version of Python 3 from the Macbook operating system directory.
The malware then ” patched” the downloaded app by comparing the modified executable with a sequence hardcoded inside Activator. If a match was found, the malware removed the initial bytes, making the application appear cracked and functional to the user. However, the true intentions of the attackers became apparent as the malware initiated its main payload.
The infected sample established communication with a command-and-control (C2) server by generating a unique Uniform Resource Locator (URL), or web address, through a combination of hardcoded words and a random third-level domain name.
This method allowed the malware to conceal its activities within normal DNS server traffic, ensuring the payload download.
The decrypted script obtained from the C2 server – a remote server or infrastructure used by cybercriminals to control and manage their malware or botnet operations – revealed that the malware operated by executing arbitrary commands received from the server. These commands were often delivered as Base64-encoded Python scripts.
Furthermore, the malware harvested sensitive information from the infected system, including the operating system version, user directories, list of installed applications, CPU type, and external IP address. The gathered data was then sent back to the server.
Malware Campaign Targets Crypto Wallet Applications
While analyzing the malware campaign, Kaspersky observed that the C2 server did not return any commands during their investigation and eventually stopped responding.
However, subsequent attempts to download the third-stage Python script led to the discovery of updates in the script’s metadata, indicating ongoing development and adaptation by the malware operators.
Additionally, the malware contained functions specifically targeting popular crypto wallet applications, such as Exodus and Bitcoin-Qt.
If these applications were detected on the infected system, the malware attempted to replace them with infected versions obtained from a different host, apple-analyzer [.]com.
These infected crypto wallets included mechanisms to steal wallet unlock passwords and secret recovery phrases from unsuspecting users.
The cybersecurity firm emphasized that malicious actors continue to distribute cracked applications to gain access to users’ computers.
By exploiting user trust during software installation, attackers can easily escalate their privileges by prompting users to enter their passwords. Kaspersky also highlighted the techniques employed by the malware campaign, such as storing the Python script inside a domain TXT record on a DNS server, demonstrating the “ingenuity” of the attackers.
Featured image from Shutterstock, chart from TradingView.com